Privacy & Security
End-to-End Encryption Explained: How Secure Are Your Messages?
In today’s digital world, protecting your messages from prying eyes is more critical than ever.
Introduction
End-to-end encryption (E2EE) is a method of secure communication that ensures only the communicating users – the sender and intended recipient – can read the messages. For details, see Wikipedia. In E2EE, data is encrypted on your device before it’s sent out and can only be decrypted on the recipient’s device. This means that no third party – whether a hacker, a government agency, or even the service provider – can access the actual content of your messages.
In an era of daily digital communication, E2EE has become vital for preserving privacy: it keeps conversations truly private by design, protecting them from prying eyes and unauthorized access. This introduction explores what E2EE is and why it’s so important for secure messaging in plain language, setting the stage for a deeper dive into how it works and how it’s used in popular apps.
How End-to-End Encryption Works
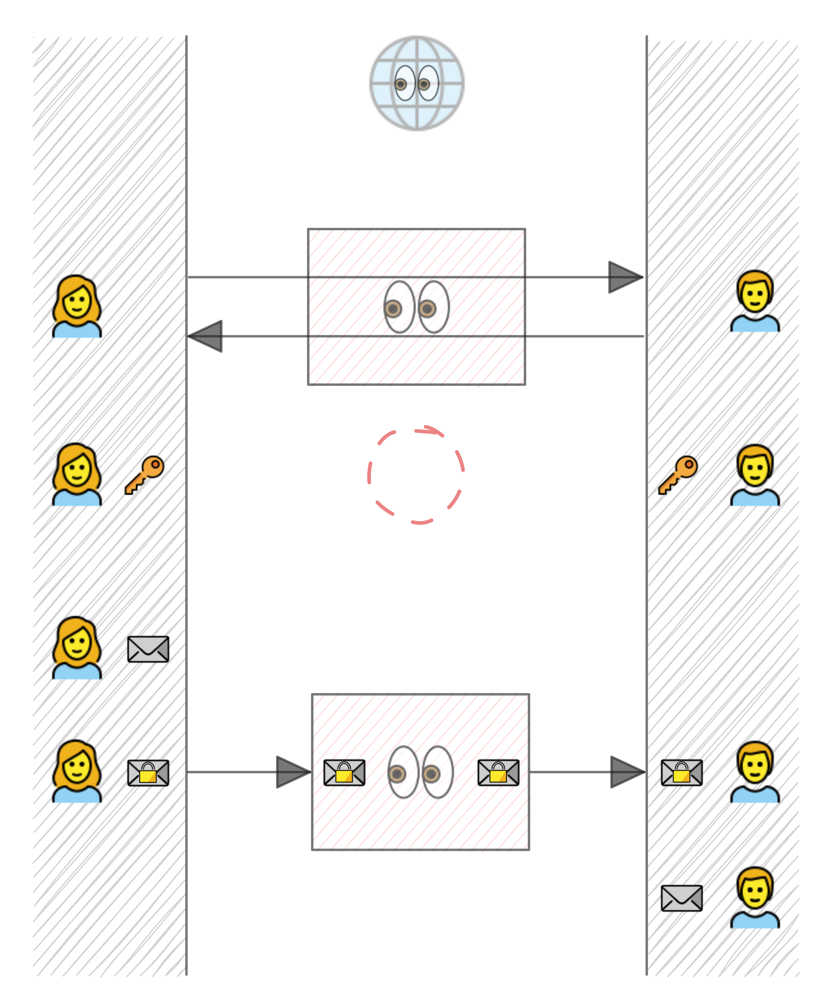
At its core, end-to-end encryption transforms readable text (plaintext) into a scrambled, unreadable format (ciphertext) using cryptographic algorithms. The magic lies in encryption keys – secret codes that lock and unlock your messages.
Encryption Keys and Secure Message Exchange
Modern E2EE typically relies on public-key cryptography (asymmetric encryption) to exchange secrets, often combined with symmetric encryption for the actual message content. Here’s how a secure E2EE conversation usually works:
- Key Generation & Sharing: When you first set up a secure messaging app, it generates a pair of cryptographic keys for you – a public key and a private key. Learn more from PCMag.
- Message Encryption: When Alice sends a message to Bob, her app uses Bob’s public key to encrypt the message on her device. This turns the plaintext message (e.g., “Hello Bob”) into ciphertext that looks like random characters. See details at PCMag.
- Transmission: The encrypted message (ciphertext) is sent over the Internet to the messaging service’s server and on to Bob. Importantly, the server never decrypts the message – it merely relays the encrypted data.
- Message Decryption: When Bob receives the message, his app uses his private key to decrypt the ciphertext back into the original message, allowing him to read it. Only Bob (the intended recipient) can perform this decryption.
Most secure messaging protocols implement these steps under the hood. For instance, the Signal Protocol (used by apps like Signal and WhatsApp) automatically handles key generation, exchange, and message encryption/decryption without user intervention. Many E2EE systems use a combination of asymmetric and symmetric encryption for efficiency.
Symmetric vs. Asymmetric Encryption: Symmetric encryption uses one secret key for both encryption and decryption. If Alice and Bob share a symmetric key, Alice can encrypt a message with that key and Bob can decrypt it with the same key. This method is fast and efficient for large amounts of data, but the challenge is securely sharing the key. In contrast, asymmetric encryption uses a pair of keys – one public and one private – where the public key encrypts data and only the matching private key can decrypt it. Learn more from NordPass.
E2EE vs. Other Encryption Methods
Not all “encrypted” messaging is truly end-to-end. It’s important to distinguish E2EE from other common encryption models:
- Encryption in Transit (Transport-Layer Encryption): Data is encrypted while traveling between your device and the service’s server. For example, TLS encrypts data en route, but once it reaches the server it is decrypted, processed, and re-encrypted. See Cloudflare’s explanation.
- Encryption at Rest: Data stored on a server is encrypted. However, since the service provider typically holds the decryption keys, they can access your messages if needed. More details can be found on Wikipedia.
By contrast, E2EE encrypts data from the moment it leaves your device until it is decrypted on the recipient’s device—with no intermediate decryption. The service provider’s servers act solely as blind pass-through agents, ensuring that no third party ever holds the decryption keys. This makes E2EE far more secure against data breaches; even if the server is hacked or subpoenaed, the attackers receive only indecipherable text. Read more on PCMag.
Security & Privacy Benefits of E2EE
- Only You and the Recipient Can Read the Message: Since the service provider doesn’t store the decryption keys, they cannot read your messages. Learn more on Wikipedia.
- Protection Against Hackers and Data Breaches: Even if attackers intercept your communication or breach a server, they cannot decrypt the content without the keys. See details on PCMag.
- Prevents Unauthorized Surveillance: E2EE stops network eavesdroppers and government agencies from accessing your message content. Read more at EFF.
- Integrity and Trust: Cryptographic authentication (such as digital signatures or key verification) ensures that messages remain unaltered in transit.
These benefits make E2EE superior to centralized encryption models, ensuring that even if a server is compromised, your data remains secure. See further explanation on Cloudflare.
Risks & Limitations of E2EE
- Metadata Exposure: While E2EE secures the content of your messages, it does not inherently hide metadata such as who you contacted, when, and how often.
- Key Management & User Responsibility: The protection offered by E2EE depends on keeping your private keys secure. Loss or compromise of these keys can expose your data.
- End-Point Security (Client Security): E2EE secures data in transit and on servers, but if your device is compromised (e.g., via malware), the decrypted messages can be accessed.
- Usability Trade-offs: Implementing features like cloud synchronization, server-side search, or cross-device backups can be challenging with E2EE.
- Myths and Misconceptions: It is a myth that E2EE is only needed if you have something to hide or that it makes you completely anonymous; it protects message content but not necessarily metadata or your online status.
In practice, while E2EE raises the bar for attackers, it must be combined with robust endpoint security and good user practices.
E2EE in Popular Messaging Apps
Many popular messaging apps have adopted end-to-end encryption, though implementations vary. The table below summarizes key details:
| Messaging App | End-to-End Encryption | Encryption Protocol / Model | Notable Security Features |
|---|---|---|---|
| Signal | Yes (default for all chats, calls, and group chats) | Signal Protocol (open-source, uses Double Ratchet for forward secrecy) | Open-source code, Safety Number verification, minimal metadata, disappearing messages |
| Yes (default for all one-on-one and group chats since 2016) | Signal Protocol under the hood | Encrypted backups (optional), security code verification, end-to-end encrypted calls – see PCMag. | |
| Apple iMessage | Yes (default if both users are on Apple devices) | Apple’s proprietary E2EE (public-key encryption tied to your Apple ID/devices) | Seamless integration on iOS/macOS, encrypted conversations, encrypted iCloud backups with Advanced Data Protection – see CISA. |
| Telegram (Secret Chats) | Optional (Secret Chats only) | MTProto (client–server encryption by default; optional E2EE for Secret Chats) | Self-destruct timers, prevention of forwarding; regular chats use cloud encryption |
| Odyssey | Yes (end-to-end encrypted by default for all communications) | Odyssey’s custom secure messaging protocol (unique key per chat) | On-device decryption, unique keys per chat, digital keys for spam prevention |
Signal
Often considered the gold standard of secure messaging, Signal was built from the ground up with privacy in mind. It uses the Signal Protocol—an open-source, peer-reviewed protocol with double ratcheting for forward secrecy. Everything is encrypted by default, and the app minimizes metadata collection. Its “Safety Numbers” feature lets users verify contacts to prevent man-in-the-middle attacks.
As the world’s most popular messaging app, WhatsApp brought E2EE to the masses in 2016. Using the Signal Protocol internally, every message and call is encrypted. While WhatsApp collects some metadata (such as sender, timestamp, and device information), the content remains inaccessible even to WhatsApp or Facebook. Features like disappearing messages and encrypted backups further enhance user privacy. Read more on PCMag.
Apple iMessage
iMessage provides end-to-end encryption by default between Apple devices using a proprietary system tied to your Apple ID and device-specific keys. While this ensures that only intended devices can decrypt messages, there are caveats: messages sent to non-Apple users fall back to unencrypted SMS/MMS, and iCloud backups can be vulnerable unless Advanced Data Protection is enabled. Apple’s recent introduction of the PQ3 protocol helps future-proof iMessage’s encryption against quantum threats.
Telegram
Telegram’s default chats use client–server encryption, meaning messages are stored on Telegram’s servers and can be accessed by them. For true E2EE, users must initiate “Secret Chats,” which are device-specific and offer features like self-destruct timers and no forwarding. However, regular chats are not end-to-end encrypted, leaving a trade-off between convenience and privacy.
Odyssey
Odyssey is an emerging secure messaging app that puts privacy front and center. It encrypts all messages by default using its custom protocol that assigns a unique key per chat. In addition to on-device message handling—ensuring messages are decrypted only on user devices—Odyssey introduces digital keys for spam prevention, requiring a digital token or handshake to initiate communication. This design provides robust confidentiality and enhanced control over your message privacy.
Government Regulations & E2EE
The widespread adoption of end-to-end encryption has sparked a global debate pitting user privacy against government and law enforcement interests. Privacy advocates and tech companies insist that strong, uncompromised encryption is essential for security and civil liberties, while some governments argue that E2EE hampers efforts to combat serious crimes (such as terrorism or child exploitation) because they cannot access criminals’ communications even with a warrant.
Encryption Backdoors and “Exceptional Access”: Many governments have proposed laws or directives that would require companies to provide backdoor access to encrypted communications. For example, the proposed EARN IT Act in the U.S. has been widely criticized for potentially forcing platforms to scan user content or weaken encryption. Experts warn that such backdoors would put massive legal pressure on companies, effectively pushing them to abandon true E2EE. Read more from EFF on the EARN IT Act.
Law enforcement agencies often refer to the challenge of “going dark” when they are unable to access encrypted data—even with a court order. While some have floated ideas like client-side scanning, privacy advocates argue that such measures would effectively break E2EE by turning your device into an informant. Learn more from EFF on side scanning.
Global Landscape: Different countries are approaching this balance in varied ways. Australia’s AA Act 2018, India’s traceability rules, and EU proposals to combat child abuse content are examples of measures that could pressure companies to compromise encryption. Meanwhile, some officials—for example, the UK’s Information Commissioner’s Office—defend the use of strong encryption for public safety. In a recent case in Brazil, authorities briefly blocked WhatsApp due to encryption challenges; see Newsmobile on Brazil.
In summary, government regulations represent one of the biggest external risks to the future of E2EE. The next few years will be critical as laws like the EARN IT Act are debated.
Future of E2EE & Secure Messaging
End-to-end encryption is not a static technology; it’s continually evolving to meet new threats and incorporate innovative solutions. As we look to the future of secure messaging, several trends are on the horizon:
- Post-Quantum Cryptography: One looming threat is the rise of quantum computing. Powerful quantum computers in the future could potentially break widely used encryption algorithms. Researchers are developing quantum-resistant (post-quantum) encryption algorithms. Messaging apps are beginning to integrate these—Signal is upgrading its protocol using quantum-resistant key exchange (incorporating CRYSTALS-Kyber) and Apple’s new PQ3 protocol for iMessage adds extra cryptographic protection.
- Advanced Cryptographic Techniques: Beyond post-quantum, enhancements such as multi-party encryption for secure group chats, zero-knowledge proofs, and metadata-resistant communication methods (e.g., mixnets or delayed message batching) are in development.
- Improved User Experience & Accessibility: As encryption becomes ubiquitous, expect more seamless key management, easier device transfers, and integration into other communication forms like email and video conferencing.
- Integration with Identity and Authentication: Future systems might shift away from relying solely on phone numbers toward more privacy-preserving identifiers and decentralized identity (DID) models.
- Secure Computing and Client-Side AI: As devices become more powerful, features like on-device spam filtering, auto-reply suggestions, and transcription may be implemented without compromising encryption.
In conclusion, the future of E2EE and secure messaging looks bright. Privacy and security concerns are at an all-time high, and user demand is pushing companies to deliver solutions that are both secure and convenient. We are likely to see E2EE become a standard feature across communication tools. Though regulatory pressures and evolving attack methods remain challenges, the technical community is committed to strengthening encryption rather than weakening it.
The bottom line is that using end-to-end encrypted services is one of the best steps you can take today to secure your messages. Going forward, these services will only get more robust. Your messages’ security isn’t just about how they’re encrypted—it’s about the entire ecosystem of privacy features built around them. The industry is innovating on all fronts to answer the question: “How secure are your messages?” with a resounding “Very secure – and getting even more so.” For more, visit Wikipedia on decryption.